In computer networking, a single
layer-2 network may be partitioned to create multiple distinct broadcast
domains, which are mutually isolated so that packets can only pass between them
via one or more routers; such a domain is referred to as a virtual local area
network, virtual LAN or VLAN.
A virtual local area network (VLAN)
is a logical group of workstations, servers and network devices that appear to
be on the same LAN despite their geographical distribution. A VLAN allows a
network of computers and users to communicate in a simulated environment as if
they exist in a single LAN and are sharing a single broadcast and multicast
domain. VLANs are implemented to achieve scalability, security and ease of
network management and can quickly adapt to change in network requirements and
relocation of workstations and server nodes.
Higher-end switches allow the
functionality and implementation of VLANs. The purpose of implementing a VLAN
is to improve the performance of a network or apply appropriate security features.
A VLAN allows several networks to
work virtually as an LAN. One of the most beneficial elements of a VLAN is that
it removes latency in the network, which saves network resources and increases
network efficiency. In addition, VLANs are created to provide segmentation and
assist in issues like security, network management and scalability. Traffic
patterns can also easily be controlled by using VLANs.
VLANs are configured through
software rather than hardware, which makes them extremely flexible. One of the
biggest advantages of VLANs is that when a computer is physically moved to
another location, it can stay on the same VLAN without any hardware
reconfiguration.
 |
| Physical View |
 |
| Logical View |
Physical n Logical View of a VLAN
VLAN's also allow broadcast domains
to be defined without using routers. Bridging software is used instead to
define which workstations are to be included in the broadcast domain. Routers
would only have to be used to communicate between two VLAN's.
VLANs can be used to partition a
local network into several distinctive segments, for example:
- Production
- Voice over IP
- Network management
- Storage area network (SAN)
- Guest network
- Demilitarized zone (DMZ)
- Client separation (ISP)
In a common infrastructure shared
across VLAN trunks can provide a very high level of security with great flexibility
for a comparatively low cost. Quality of Service schemes can optimize traffic
on trunk links for realtime (VoIP) or low-latency requirements (Storage Area Network).
History?
After successful experiments with
Voice over Ethernet from 1981 to 1984, Dr. W. David Sincoskie joined Bellcore
and began addressing the problem of scaling up Ethernet networks. At 10 Mbit/s,
Ethernet was faster than most alternatives at the time; however, Ethernet was a
broadcast network and there was no good way of connecting multiple Ethernet
networks together. This limited the total bandwidth of an Ethernet network to
10 Mbit/s and the maximum distance between any two nodes to a few hundred feet.
Why use VLAN's?
VLAN's offer a number of advantages
over traditional LAN's. They are:
- Performance
In networks where traffic consists
of a high percentage of broadcasts and multicasts, VLAN's can reduce the need
to send such traffic to unnecessary destinations. For example, in a broadcast
domain consisting of 10 users, if the broadcast traffic is intended only for 5
of the users, then placing those 5 users on a separate VLAN can reduce traffic
.
.
Compared to switches, routers
require more processing of incoming traffic. As the volume of traffic passing
through the routers increases, so does the latency in the routers, which
results in reduced performance. The use of VLAN's reduces the number of routers
needed, since VLAN's create broadcast domains using switches instead of
routers.
- Formation of Virtual Workgroups
Nowadays, it is common to find
cross-functional product development teams with members from different
departments such as marketing, sales, accounting, and research. These
workgroups are usually formed for a short period of time. During this period,
communication between members of the workgroup will be high. To contain
broadcasts and multicasts within the workgroup, a VLAN can be set up for them.
With VLAN's it is easier to place members of a workgroup together. Without
VLAN's, the only way this would be possible is to physically move all the
members of the workgroup closer together.
However, virtual workgroups do not
come without problems. Consider the situation where one user of the workgroup
is on the fourth floor of a building, and the other workgroup members are on
the second floor. Resources such as a printer would be located on the second
floor, which would be inconvenient for the lone fourth floor user.
Another problem with setting up virtual workgroups is the implementation of centralized server farms, which are essentially collections of servers and major resources for operating a network at a central location. The advantages here are numerous, since it is more efficient and cost-effective to provide better security, uninterrupted power supply, consolidated backup, and a proper operating environment in a single area than if the major resources were scattered in a building. Centralized server farms can cause problems when setting up virtual workgroups if servers cannot be placed on more than one VLAN. In such a case, the server would be placed on a single VLAN and all other VLAN's trying to access the server would have to go through a router; this can reduce performance.
- Simplified Administration
Seventy percent of network costs
are a result of adds, moves, and changes of users in the network [ Buerger].
Every time a user is moved in a LAN, recabling, new station addressing, and
reconfiguration of hubs and routers becomes necessary. Some of these tasks can
be simplified with the use of VLAN's. If a user is moved within a VLAN,
reconfiguration of routers is unnecessary. In addition, depending on the type
of VLAN, other administrative work can be reduced or eliminated [ Cisco white
paper]. However the full power of VLAN's will only really be felt when good
management tools are created which can allow network managers to drag and drop
users into different VLAN's or to set up aliases.
Despite this saving, VLAN's add a
layer of administrative complexity, since it now becomes necessary to manage
virtual workgroups.
- Reduced Cost
VLAN's can be used to create
broadcast domains which eliminate the need for expensive routers.
- Security
Periodically, sensitive data may be
broadcast on a network. In such cases, placing only those users who can have
access to that data on a VLAN can reduce the chances of an outsider gaining
access to the data. VLAN's can also be used to control broadcast domains, set
up firewalls, restrict access, and inform the network manager of an intrusion.
VLANs also have some disadvantages
and limitations as listed below:
- High risk of virus issues because one infected system may spread a virus through the whole logical network.
- Equipment limitations in very large networks because additional routers might be needed to control the workload.
- More effective at controlling latency than a WAN but less efficient than a LAN.
Establishing VLAN Memberships?
The two common approaches to
assigning VLAN membership are as follows:
- Static VLANs
- Dynamic VLANs
Static VLANs are also referred to
as port-based VLANs. Static VLAN assignments are created by assigning ports to
a VLAN. As a device enters the network, the device automatically assumes the
VLAN of the port. If the user changes ports and needs access to the same VLAN,
the network administrator must manually make a port-to-VLAN assignment for the
new connection.
Dynamic VLANs are created using
software. With a VLAN Management Policy Server (VMPS), an administrator can
assign switch ports to VLANs dynamically based on information such as the
source MAC address of the device connected to the port or the username used to
log onto that device. As a device enters the network, the switch queries a
database for the VLAN membership of the port that device is connected to.
Types of VLAN's
VLAN membership can be classified
by port, MAC address, and protocol type:
- Layer 1 VLAN: Membership by Port
Membership in a VLAN can be defined
based on the ports that belong to the VLAN. For example, in a bridge with four
ports, ports 1, 2, and 4 belong to VLAN 1 and port 3 belongs to VLAN 2.
Port
|
VLAN
|
1
|
1
|
2
|
1
|
3
|
2
|
4
|
1
|
Assignment of ports to different
VLAN's
The main disadvantage of this method is that it does not allow for user mobility. If a user moves to a different location away from the assigned bridge, the network manager must reconfigure the VLAN.
- Layer 2 VLAN: Membership by MAC
Address
Here, membership in a VLAN is based
on the MAC address of the workstation. The switch tracks the MAC addresses
which belong to each VLAN (see Figure4). Since MAC addresses form a part of the
workstation's network interface card, when a workstation is moved, no reconfiguration
is needed to allow the workstation to remain in the same VLAN. This is unlike
Layer 1 VLAN's where membership tables must be reconfigured.
MAC Address
|
VLAN
|
1212354145121
|
1
|
2389234873743
|
2
|
3045834758445
|
2
|
5483573475843
|
1
|
Assignment of MAC addresses to
different VLAN's
The main problem with this method is that VLAN membership must be assigned initially. In networks with thousands of users, this is no easy task. Also, in environments where notebook PC's are used, the MAC address is associated with the docking station and not with the notebook PC. Consequently, when a notebook PC is moved to a different docking station, its VLAN membership must be reconfigured.
- Layer 2 VLAN: Membership by
Protocol Type
VLAN membership for Layer 2 VLAN's
can also be based on the protocol type field found in the Layer 2 header.
Protocol
|
VLAN
|
IP
|
1
|
IPX
|
2
|
Assignment of protocols to
different VLAN's
- Layer 3 VLAN: Membership by IP Subnet
Address
Membership is based on the Layer 3
header. The network IP subnet address can be used to classify VLAN membership.
IP Subnet
|
VLAN
|
23.2.24
|
1
|
26.21.35
|
2
|
Assignment of IP subnet addresses
to different VLAN's
Although VLAN membership is based on Layer 3 information, this has nothing to do with network routing and should not be confused with router functions. In this method, IP addresses are used only as a mapping to determine membership in VLAN's. No other processing of IP addresses is done.
In Layer 3 VLAN's, users can move their workstations without reconfiguring their network addresses. The only problem is that it generally takes longer to forward packets using Layer 3 information than using MAC addresses.
- Higher Layer VLAN's
It is also possible to define VLAN
membership based on applications or service, or any combination thereof. For
example, file transfer protocol (FTP) applications can be executed on one VLAN
and telnet applications on another VLAN.
The 802.1Q draft standard defines
Layer 1 and Layer 2 VLAN's only. Protocol type based VLAN's and higher layer
VLAN's have been allowed for, but are not defined in this standard. As a
result, these VLAN's will remain proprietary.
Types of Connections?
Devices on a VLAN can be connected
in three ways based on whether the connected devices are VLAN-aware or
VLAN-unaware. Recall that a VLAN-aware device is one which understands VLAN
memberships (i.e. which users belong to a VLAN) and VLAN formats.
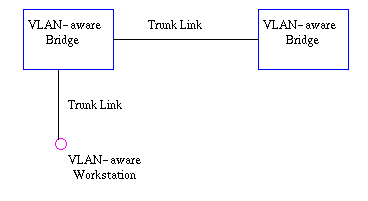
- Trunk Link
All the devices connected to a
trunk link, including workstations, must be VLAN-aware. All frames on a trunk
link must have a special header attached. These special frames are called
tagged frames.
- Access Link
An access link connects a
VLAN-unaware device to the port of a VLAN-aware bridge. All frames on access
links must be implicitly tagged (untagged). The VLAN-unaware device can be a
LAN segment with VLAN-unaware workstations or it can be a number of LAN
segments containing VLAN-unaware devices (legacy LAN).
This is a combination of the
previous two links. This is a link where both VLAN-aware and VLAN-unaware
devices are attached. A hybrid link can have both tagged and untagged frames,
but allthe frames for a specific VLAN must be either tagged or untagged.
It must also be noted that the network can have a
combination of all three types of links.
Protocol-based VLANs?
In a switch that supports
protocol-based VLANs, traffic is handled on the basis of its protocol.
Essentially, this segregates or forwards traffic from a port depending on the
particular protocol of that traffic; traffic of any other protocol is not forwarded
on the port.
For example, it is possible to
connect the following to a given switch:
- A host generating ARP traffic to port 10
- A network with IPX traffic to port 20
- A router forwarding IP traffic to port 30
If a protocol-based VLAN is created
that supports IP and contains all three ports, this prevents IPX traffic from
being forwarded to ports 10 and 30, and ARP traffic from being forwarded to
ports 20 and 30, while still allowing IP traffic to be forwarded on all three
ports.
Protocols and design?
- IEEE 802.1Q
- Cisco VLAN Trunking Protocol (VTP)
- Multiple VLAN Registration Protocol
- Shortest Path Bridging
Default Ethernet VLAN Configuration
The switch module supports only
Ethernet interfaces. Table shows the default configuration for Ethernet
VLANs.
Creating or Modifying an Ethernet VLAN
To access VLAN configuration mode,
enter the vlan global configuration command with a VLAN ID. Enter a new VLAN ID
to create a VLAN, or enter an existing VLAN ID to modify that VLAN. You can use
the default VLAN configuration or enter commands to configure the VLAN.
Switch# configure terminal
Switch(config)# vlan 20
Switch(config-vlan)# name test20
Switch(config-vlan)# end
Assigning Static-Access Ports to a VLAN
You can assign a static-access port
to a VLAN.
Switch# configure terminal
Enter configuration commands, one per line. End with
CNTL/Z.
Switch(config)# interface fastethernet0/1
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 2
Switch(config-if)# end
Configuring a Trunk Port
Beginning in privileged EXEC mode,
follow these steps to configure a port as an 802.1Q trunk port:
Switch# configure terminal
Enter configuration commands, one per line. End with
CNTL/Z.
Switch(config)# interface fastethernet0/2
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport trunk native vlan 33
Switch(config-if)# end
----







No comments:
Post a Comment